


Next: Experimental Framework
Up: Evaluation Methodology
Previous: Software Encryption
For hardware encryption we propose to do the following
- 1.
- Speed of encryption
Can a hardware implementation be fast enough to match the network
bandwidth ?
If the software encryption does not match the network speed but the
hardware encryption does, then this study becomes relevant.
Proposed table :
Bandwidth vs Speed of encryption(time to encrypt one bit).
It must be noted here that the hardware implementation of a particular
encryption algorithm is independent of the device on which it is
present.
We will study this using available optimized hardware implementations.
The feasibility of universal encryption here can easily be defined.
- 2.
- Costs of hardware encryption (power and chip area)
How costly is hardware encryption with respect to network
interfaces?
Proposed table:
We analyze costs of hardware implementations with respect to standard
network interfaces. This cost can be categorized as
- Additional Power - Power consumed by the network interface vs
Power consumed by the hardware module on the interface
- Chip area - Chip area required for the network interface vs Chip
space required for the hardware module
This table will answer the question of whether it is economically
feasible to incorporate an encryption co-processor into the network
interface card, thereby enabling universal encryption.
In this case, the ratio of hardware costs to network interfaces costs
should be very low.
A rough estimate of performance gathered from various sources
[Schneier99,Goodman] is as shown in figures 1 and 2.
Figure 1:
Speed of Software encryption, Bandwidth vs CPU
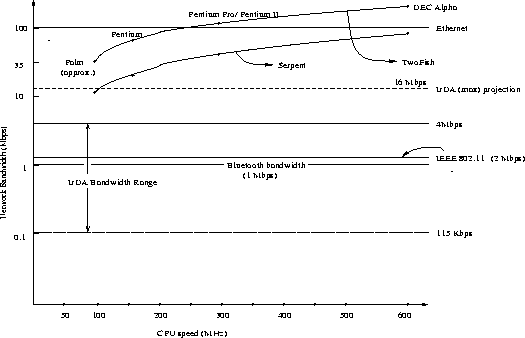 |
Figure 2:
Power consumed for software encryption
 |
It must be noted that the graph is only a rough approximation,
not necessarily reflecting accurate values. We propose to use the
above graphs as a guiding factor for our experimental framework.
This framework will refine the above graphs using simulations where
possible (Eg, software encryption performance). For hardware
encryption, at the moment we plan to use only results obtained by
researchers elsewhere.



Next: Experimental Framework
Up: Evaluation Methodology
Previous: Software Encryption
Ramadass Nagarajan
2000-03-21
