 |
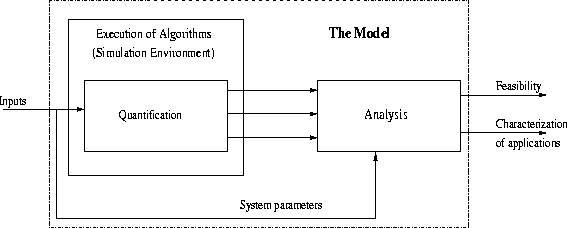
The framework is envisioned as in Figure 3,
The inputs to the experimental framework are the various system parameters. The framework uses a simulation environment that takes these inputs and quantifies the costs of each one of the desired/defined performance metrics. It then uses these quantified metrics and analyses them for feasibility and also gives a precise characterization of the kind of applications for which strong encryption can be sustained. The outputs would include the kind of graphs described earlier.
The analysis of software encryption can be done as follows. There are C optimised algorithms in public domain for most encryption strategies. We will use these algorithms and compile them for a target architecture to generate the instruction trace. This can then be directly translated to performance costs with respect to speed and power consumption, given the device parameters. We also stress that in a few cases, for eg, pentium class machines, such data is already available. So we will do this only for cases where such data is not available. These include analysis for portables. We take ARM as the general processor class on these machines and will do the analysis. Future trends can be approximated with a projected IPC and clock rate estimation.
At present, for hardware analysis, we only plan to use results obtained elsewhere. We will use only existing optimised hardware implementations for standard enryption algorithms. We also plan to look into the current work done by the CART group of the University of Texas, Austin, in analysing hardware performance for future technologies.